Complete cyber defence and threat visibility to protect your business
Increase your investigative power with advanced AI tools
Comprehensive enterprise threat investigations
Ripjar Cyber Investigator is designed to help organisations with the complex challenge of mitigating cyber threats from both internal and external sources.
Threat intelligence
Quickly expose the impact of malicious activity, using automation to build connections across local and remote data sources and your derived knowledge store.
Threat hunting
Proactively identify early threat indicators against your network or corporate security, and share intelligence with colleagues and partners.
Incident response
Analyse details of incidents by consolidating multiple data feeds and intelligence to understand potential impact.
Strategic analysis and forecasting
Going far beyond standard tactical analysis, Ripjar Cyber Investigator provides you with detailed, actionable intelligence based on trend and pattern analysis, to aid forecasting and long-term planning.
Designed for flexibility and compatibility
Created to seamlessly integrate with your existing operations and evolve to meet your exact requirements, Ripjar Cyber Investigator puts the power in your hands.
Powerful investigations
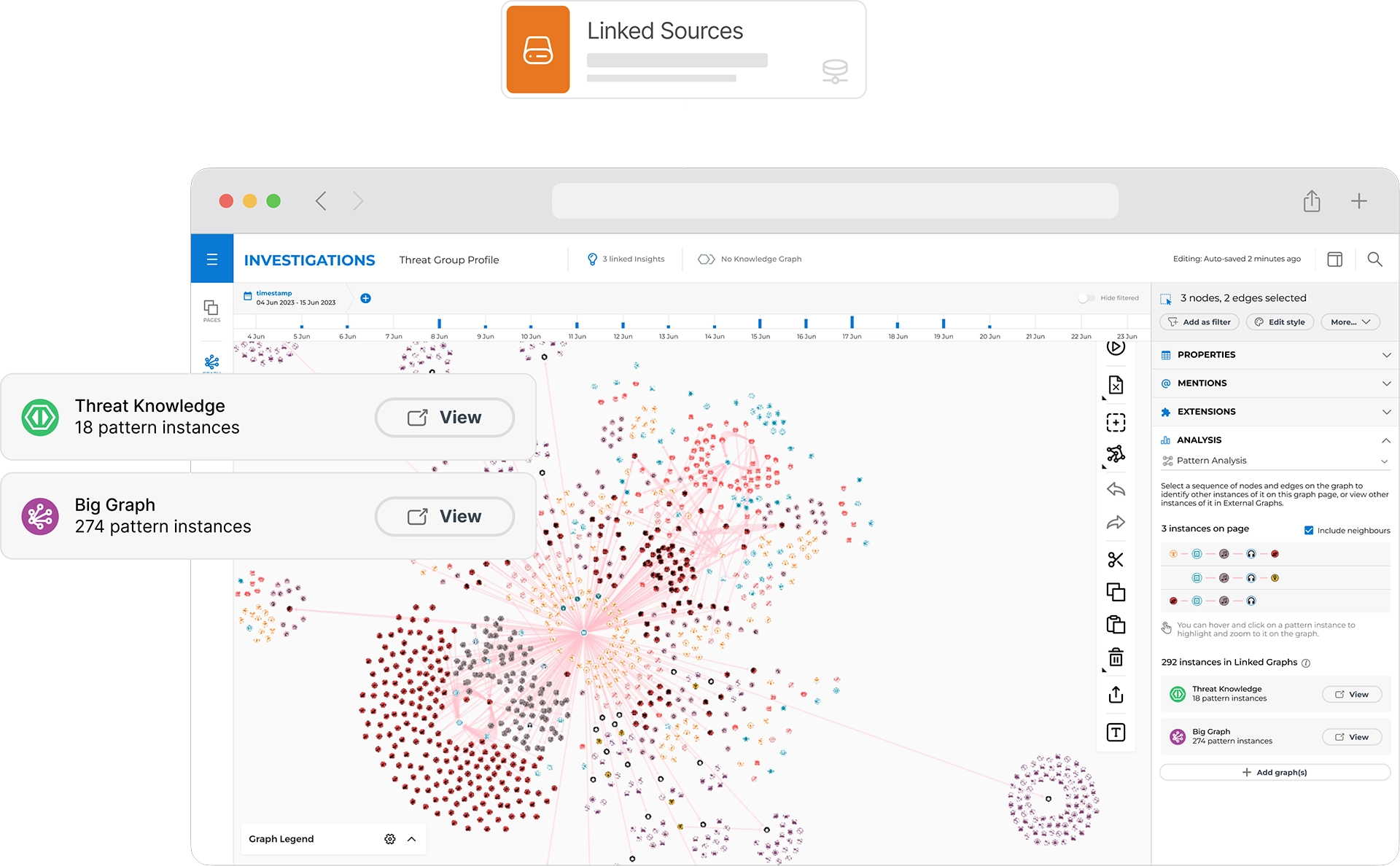
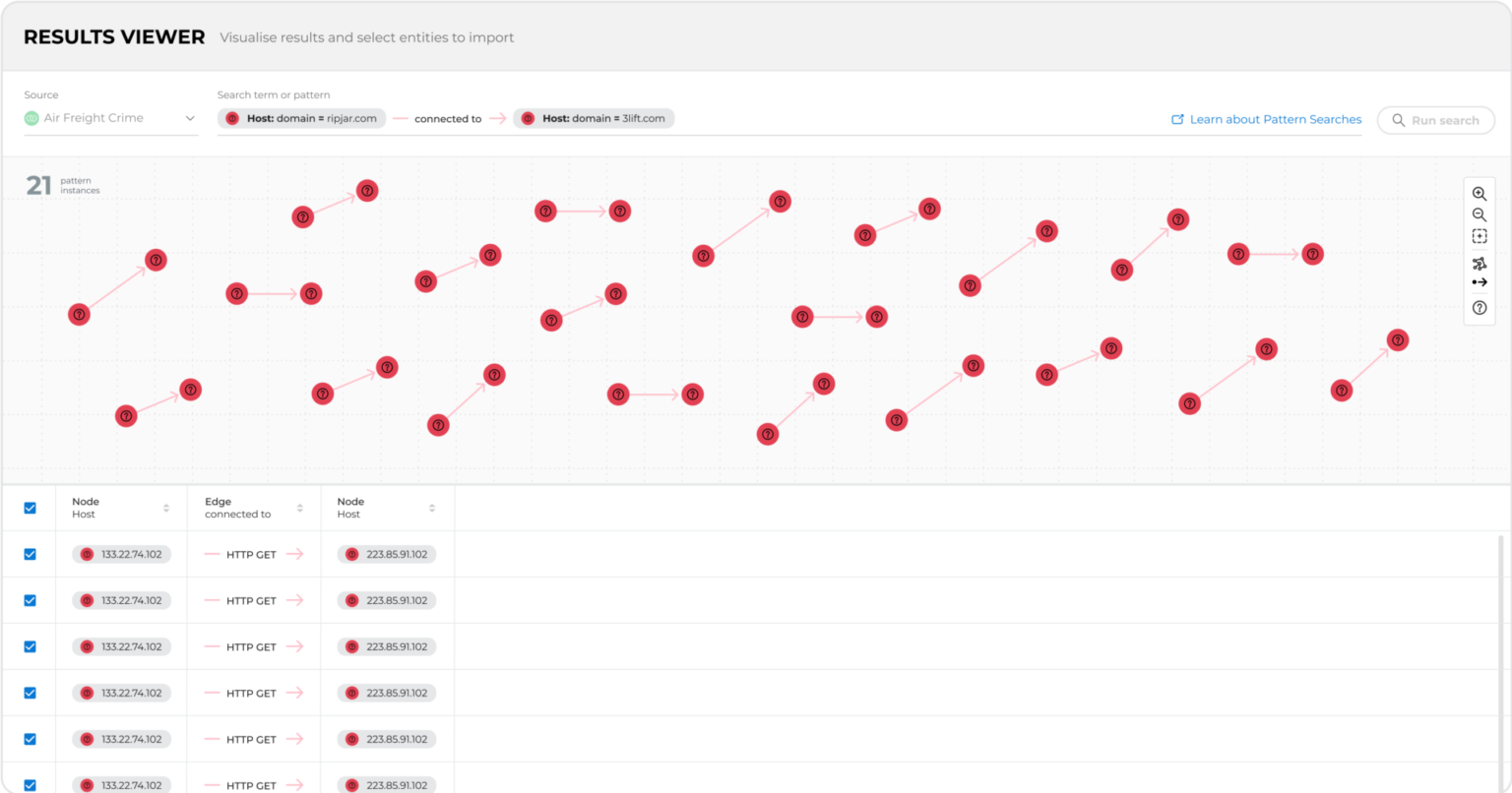
Ripjar Cyber Investigator provides everything you need to undertake powerful investigations. Use Ripjar's powerful search to retrieve data from across local and remote sources, and follow connections to discover underlying links.
Entity extraction
Gain unparalleled understanding of your data with comprehensive, AI-powered entity extraction and classification across your unstructured documents and reports.
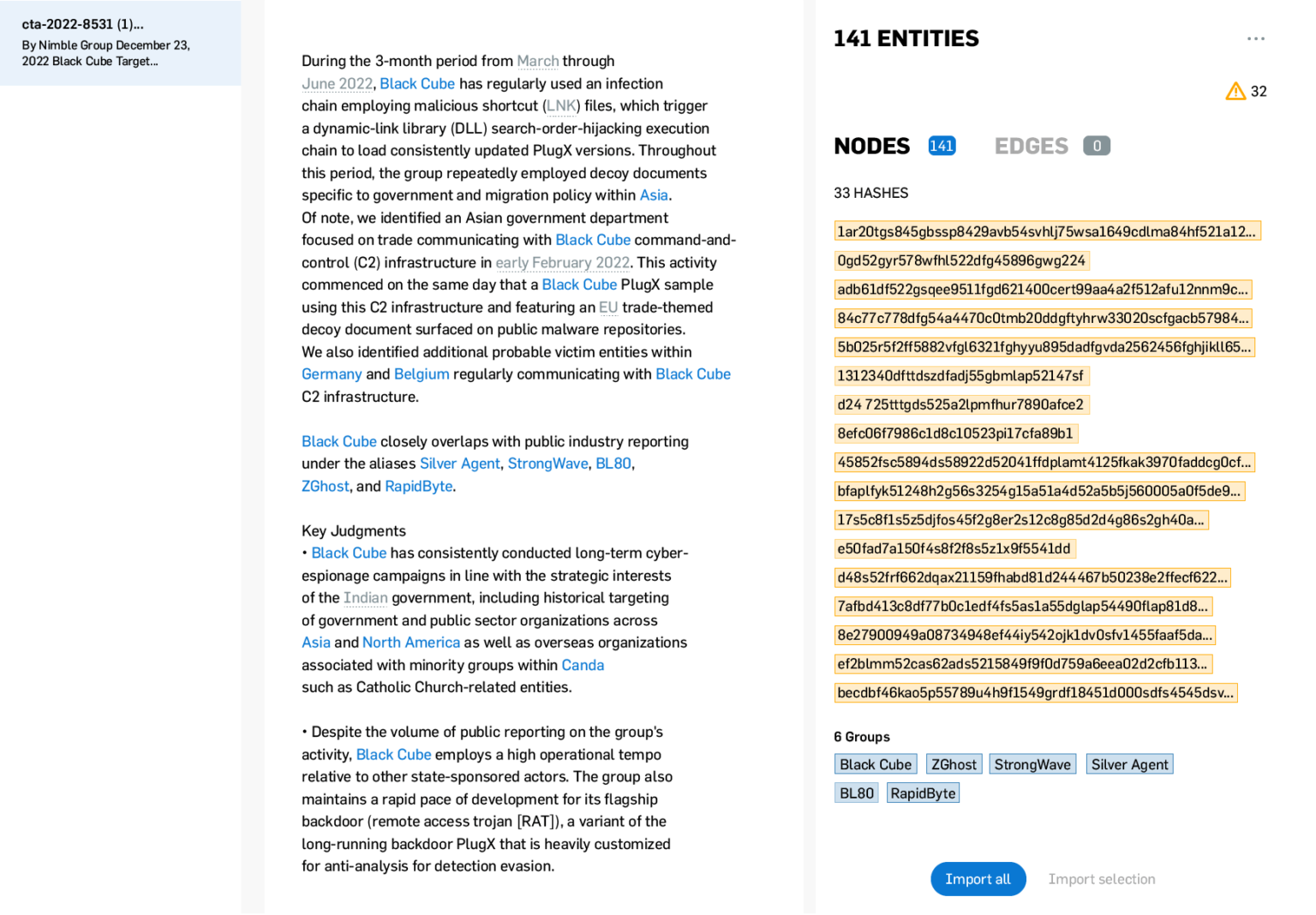
Knowledge management
Annotate findings from your investigations directly on top of fused data sources, with full lineage back to underlying data. Collate and record intelligence in a vetted organisational knowledge graph to support smarter decision-making and aid future investigations.
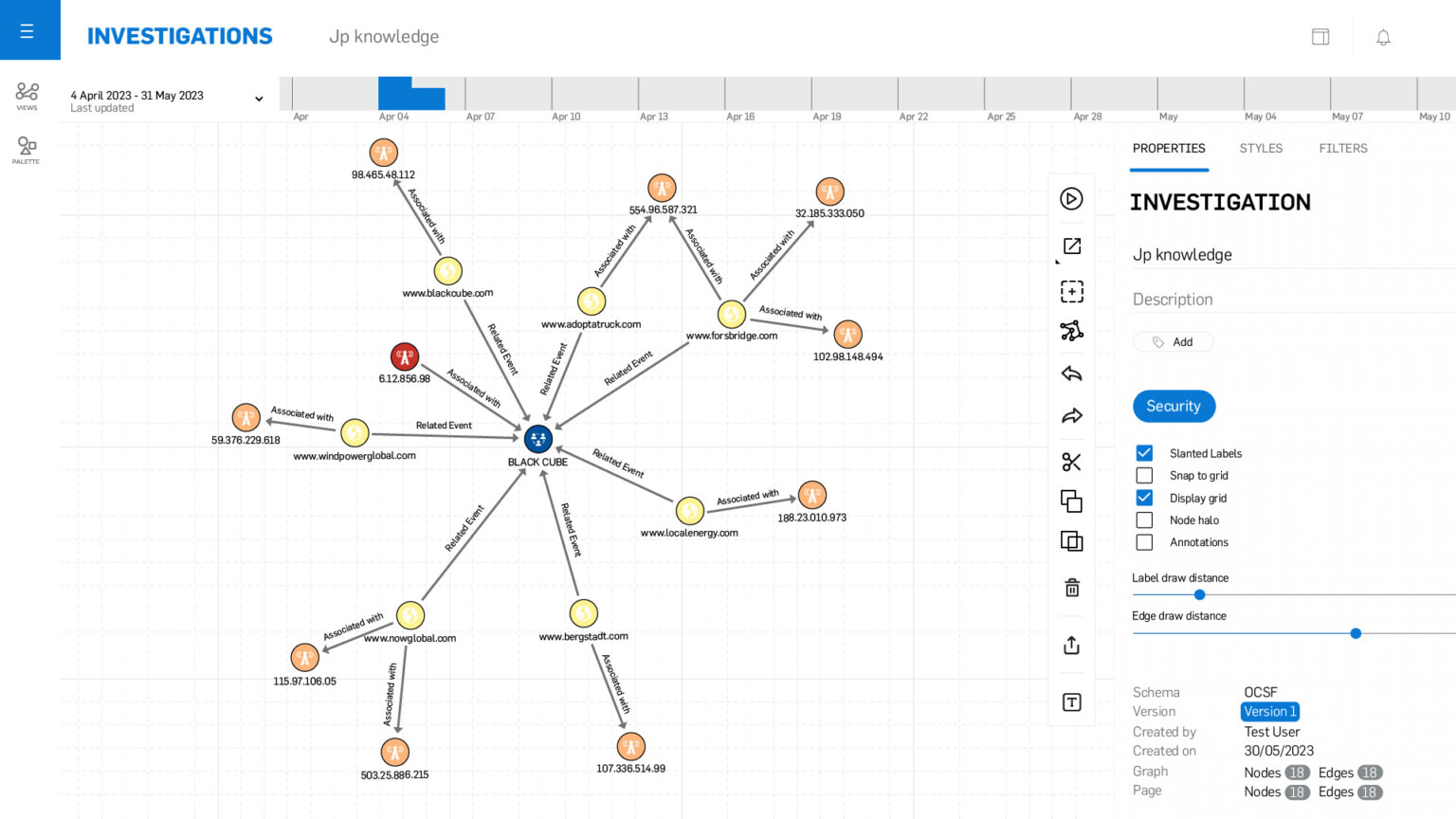
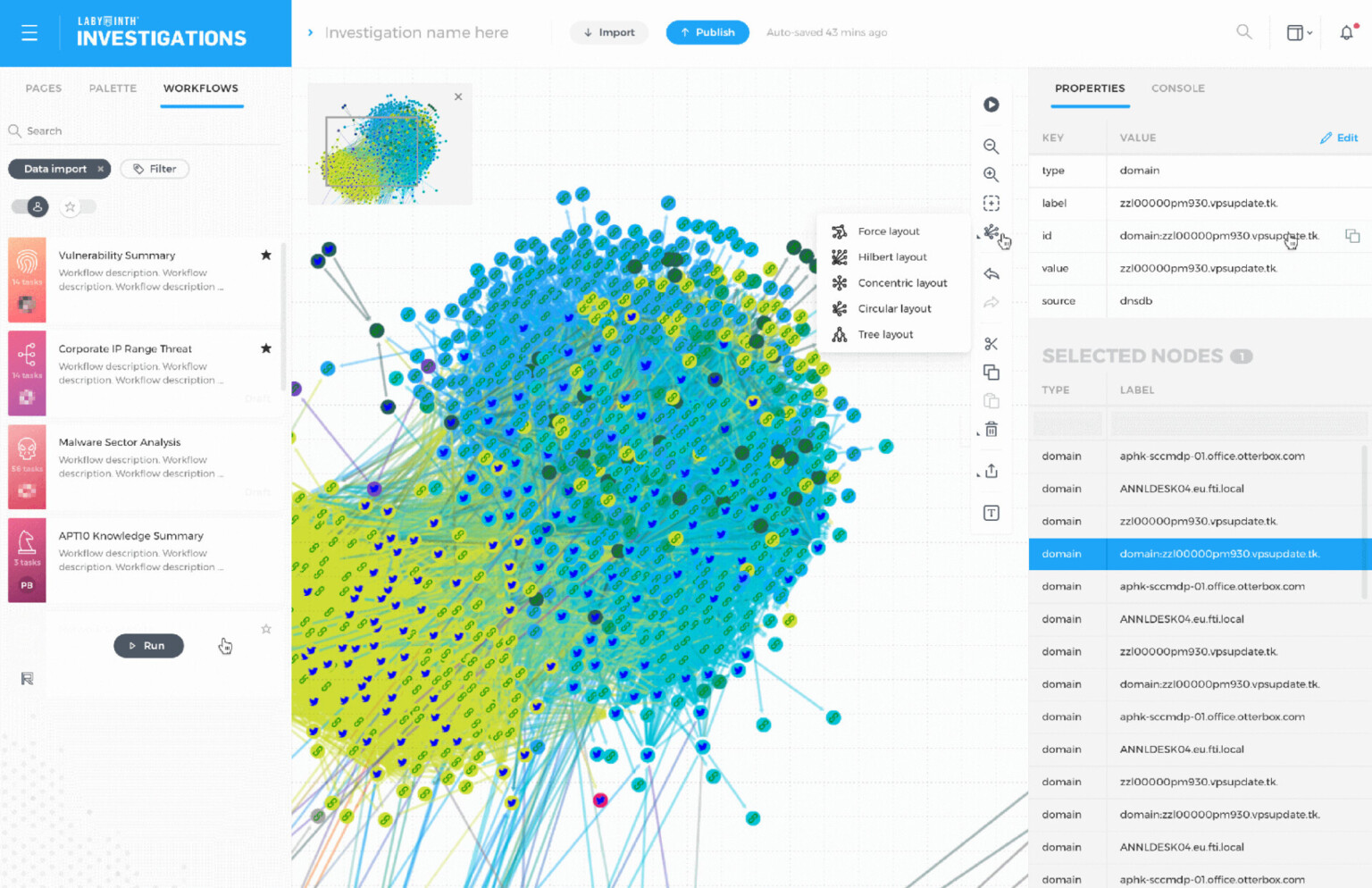
Data visualisation
Use maps, histograms, timelines, topic visualisations, hypergraphs and integrations to interpret data in context, segmenting information logically, geographically and by time-slice.
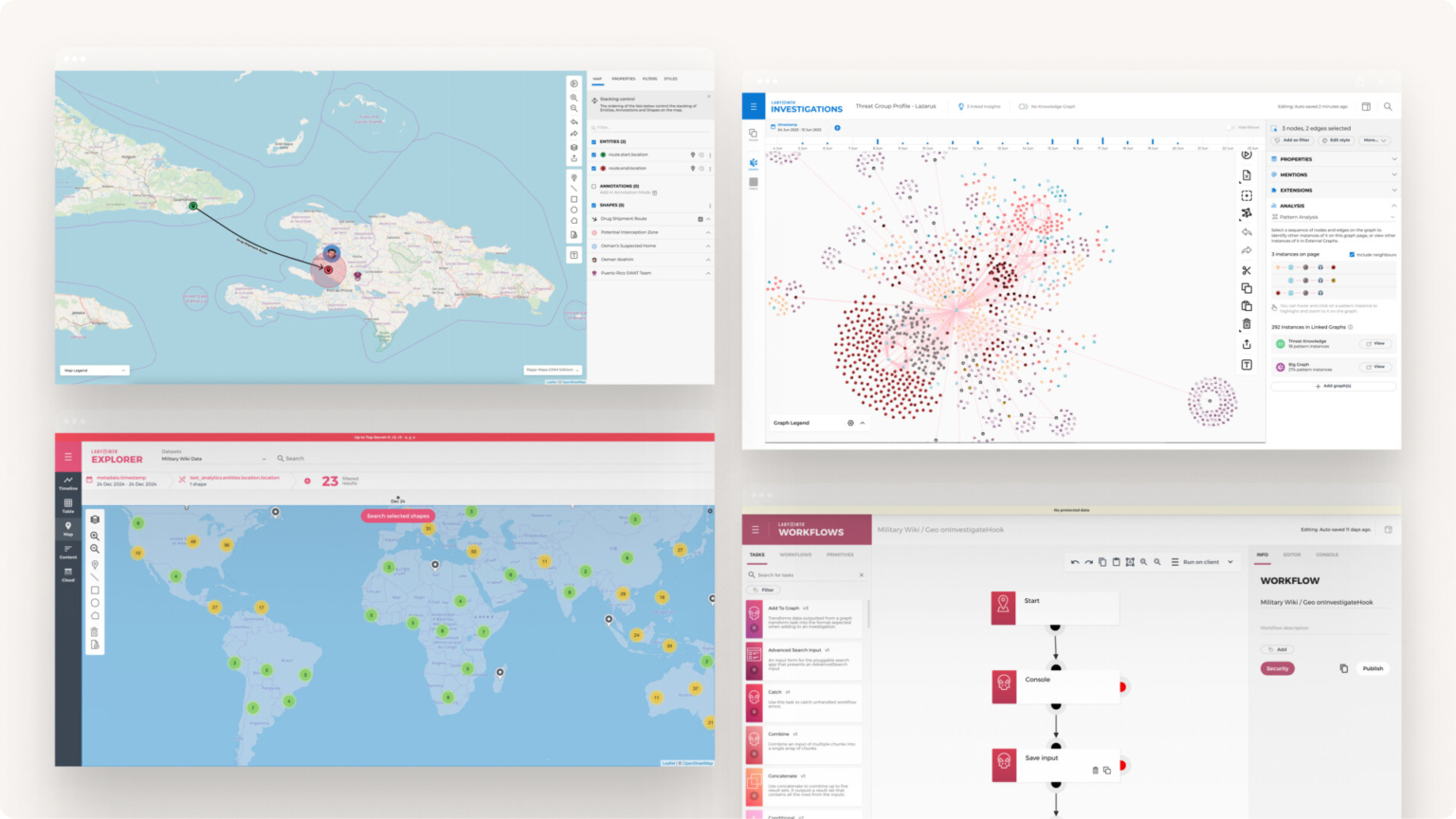
Scalable platform
Ripjar Cyber Investigator can scale to meet data volume challenges and increasing user numbers. It enables you to connect directly to big data stores with billions of entities, import data to datasets and visualise networks in the graph view.
Built-in security
Ripjar's security model has been developed to suit the most complex environments containing mixed classification documents, and the platform is capable of meeting even the strictest security requirements.

Trusted by global businesses
"Ripjar's tool is a really great platform to do analytic work in. It also has much greater knowledge capability compared to other platforms and provides us with vital forecasting ability."
Head of Threat Investigations, Fortune 500 Tech Company
"It is essential to have an approach that addresses all threats - not just cyber."
Head of Threat Investigations, Major Tech Company
Flexible workflows and automation
Ready to
get started?
Our experts are available to talk through your requirements, answer questions, and set up a demo.